Python is the only language which provides a better interface for the analysts who are working in forensics departments. It is a high level language. The analyst can write scripts in order to examine the different evidence. In the past many analysts have written open-source scripts which got rapidly used by the world in forensic investigation. For example, volatility tool for the memory forensics analysis, GRR, which is a rapid incident response framework, libppf, which is a helpful tool to access the personal files and folders. This paper will provide you the introduction to different areas of forensics in which python is used as a scripting language. Then I will develop an artefact in which I will create a python tool which will be used in forensics to analyse PE file format which is known as portable executable file attributes. Quickly generate using Python to further examine the evidence.
1. Introduction
There are lots of forensics tools available in the market. If you want to find a tool which can work as an incident response framework, or if you want to find a tool which can calculate the hash and metadata of any executable, all you need to do is to go on Google and you will quickly find those tools. There are a range of python tools available from network forensics to debugging, reverse engineering, fuzzing, web, malware, forensics to PDF file analysis (Ari 2007). One common problem with all those tools is they are separated. According to this project, if I want to analyse any portable executable, then I will have to run different tools for hash calculation, metadata extraction, string analysis etc...
There are lots of forensics tools available in the market. If you want to find a tool which can work as an incident response framework, or if you want to find a tool which can calculate the hash and metadata of any executable, all you need to do is to go on Google and you will quickly find those tools. There are a range of python tools available from network forensics to debugging, reverse engineering, fuzzing, web, malware, forensics to PDF file analysis (Ari 2007). One common problem with all those tools is they are separated. According to this project, if I want to analyse any portable executable, then I will have to run different tools for hash calculation, metadata extraction, string analysis etc...
In response to this problem, I am presenting “PEextract” tool in order to analyse the portable executable files. In the following sections you will know how python scripting language is used in different areas of forensic investigation separately. Here I am providing you one stop solution by developing an artefact PEextract. Do you want to extract the metadata of PE file? Do you want to extract and analyse the stings within exe file? Do you want to find which the suspicious dlls are and API functions imported in a given particular exe file? Then this tool is a one stop solution for you. Due to its robust features, it provides depth techniques for any PE file. In order to create this tool, I will take help of one another python file named “PEfile”. It is a python module which reads and analyses the different executable files. By using that file and by implementing my custom code I will make a robust output. I will also support my artefact by testing this tool with various executable files.
2. Overview of Draft
In this draft I am going to explain each and every things chapter wise. In chapter 4, I am giving you an overview of python programming language and how it can be helpful in forensics investigation. In chapter 5, I have explained various benefits of python programming language over other scripting language in context of forensics investigation. Chapter 6 describes the overview of different areas in which python can be used. My artefact development starts from chapter 7 in which I am going to give an overview of PE file format. I am digging deep into the PE file and format in chapter 9 and 10. Chapter 11 introduces my tool named PEextract. Which are the various features and how to implement them using python and how to test those feature of my tool has been explained in chapter 12. For testing purpose I have taken 3 different PE files and I am testing them using my tool. I am also evaluating the results. This is portable tool. However which are the things one should keep in mind while moving this tool, is mentioned in chapter 14. Chapter 15 concludes whole project with future work, conclusion and recommendation.
3. Background
On February 2005, 30 year old murder mystery got solved by police forensics investigator named randy stone. Before this day, the KSAS television station gave 3.5 inch floppy from the BTK killer. They specifically named this killer BTK, which means Bind, torture and kill the killer. That disk was containing a file named Test.A.rtf (Ari 2007). That was a normal file which was containing information about BTK killer who was responsible for 10 murders. By investigating much into that, the analyst also analysed that there is some more information stored within the file but it is not visible. That was metadata. In metadata, there was information about the physical location where a user saved this file last. Narrowed investigation leads it to one man named Denis Rader. With the help of warrant, police tried to confirm the DNA sample of his daughter and luckily it got matched (Ari 2007). Thus, how they confirmed that Denis Rader was the man who was a BTK killer.
On February 2005, 30 year old murder mystery got solved by police forensics investigator named randy stone. Before this day, the KSAS television station gave 3.5 inch floppy from the BTK killer. They specifically named this killer BTK, which means Bind, torture and kill the killer. That disk was containing a file named Test.A.rtf (Ari 2007). That was a normal file which was containing information about BTK killer who was responsible for 10 murders. By investigating much into that, the analyst also analysed that there is some more information stored within the file but it is not visible. That was metadata. In metadata, there was information about the physical location where a user saved this file last. Narrowed investigation leads it to one man named Denis Rader. With the help of warrant, police tried to confirm the DNA sample of his daughter and luckily it got matched (Ari 2007). Thus, how they confirmed that Denis Rader was the man who was a BTK killer.
In the above case study, metadata forensics investigation proved that how it can be helpful to investigate and solve 30 year old murder mystery. Currently, many tools are available in this scripting language which is helpful in a forensic investigation, such as registry decoder. This tool performs browsing, analysis, reporting and searching the different hive contents of the registry. One another research into this field is rescaling. This tool is basically an editor for the windows application developers. It can edit x64/x84 PE file attribute formats.
However, these tools don’t provide metadata and version information. They are not helpful in string analysis and hash analysis. This is the reason that I am creating this tool which will use PEfile as a reference and combining my custom code and PEfile it produces robust output for analysing PE files.
4. Python – A Comprehensive and Flexible Programming Language
As I am going to create a tool in python scripting language. I have to learn certain things before digging deep into python. Python is a multi-paradigm scripting language. Compare to Java, this programming language saves much time and space. It is a dynamic language. In this we do not need to declare variables we were doing in other programming languages like Java, c etc... It is code readable language. One can understand the whole code by even reading it.
To develop my artefact, I need to learn about the python modules. Python has a comprehensive list of standard libraries.
By default python comes with standard libraries which can helpful for developer in order to fulfil his/her task, such as access to the I/O operations, function types, string types, data types, file access directory, data compression, file formats, cryptographic services etc.. User can contribute library modules within the python (Modules).
Python is a comprehensive and flexible language due to its robust libraries. In this section I am going to discuss the overview of the various areas in which python can be useful as a scripting language. Python is a flexible and comprehensive language because we can do Cryptography and hash conversation using it. We can extract metadata information, string analysis information, API and imported DLL file information from any packed executable file. Not only this by using python we can examine *.nix and Microsoft operating system artefacts. We can also track email and web based client using python. Not only this, but also we can create tools which send requests to the server, such as Scappy (Biondi 2005). We can also create footprinting application using python. Due to having all these varieties in python, I preferred this language for my artefact development.
5. Forensics Investigation Using Python
If the investigator and his/her tools produces better and efficient effect, then and only then computer forensics investigation can be proved good. In an investigation, many times it does happen that investigator comes up with some difficult questions and they do not have any tool to answer those questions. This is the time on which they should enter in the world of python where small as well as big problems can be solved with small amount of user friendly portable code. So as I have already discussed previously, there are many benefits of using python. So let us dive into the world of python (Connor 2010).
6. Overview of Different Areas of Investigation Using Python
In this section I am going to talk about different areas of information security, in which we can implement python successfully in order to deploy the tool. As you all know python is a programming language one can build thousands of things using python. However this section differentiates traditional programmers and security coders. I am discussing different areas of security world in which we can do python coding. This section will really help you to build your base. Also I am going to use this knowledge in order to deploy my tool efficiently.
Python is a comprehensive and flexible language due to its robust libraries. In this section I am going to discuss the overview of the various areas in which python can be useful as a scripting language. Python is a flexible and comprehensive language because we can do Cryptography and hash conversation using it. We can extract metadata information, string analysis information, API and imported DLL file information from any packed executable file. Not only this by using python we can examine *.nix and Microsoft operating system artefacts. We can also track email and web based client using python. Not only this, but also we can create tools which send requests to the server, such as Scappy (Biondi 2005). We can also create footprinting application using python. Due to having all these varieties in python, I preferred this language for my artefact development.
5. Forensics Investigation Using Python
If the investigator and his/her tools produces better and efficient effect, then and only then computer forensics investigation can be proved good. In an investigation, many times it does happen that investigator comes up with some difficult questions and they do not have any tool to answer those questions. This is the time on which they should enter in the world of python where small as well as big problems can be solved with small amount of user friendly portable code. So as I have already discussed previously, there are many benefits of using python. So let us dive into the world of python (Connor 2010).
6. Overview of Different Areas of Investigation Using Python
In this section I am going to talk about different areas of information security, in which we can implement python successfully in order to deploy the tool. As you all know python is a programming language one can build thousands of things using python. However this section differentiates traditional programmers and security coders. I am discussing different areas of security world in which we can do python coding. This section will really help you to build your base. Also I am going to use this knowledge in order to deploy my tool efficiently.
6.1 Cryptography, Hash Calculation Using Python
Python provides great cryptographic services. There are inbuilt cryptography modules written in python. These are the packages which contains the information of different encryption algorithms such as AES. If you download python and install it, then they are not distributed directly with the python. However they are available separately. Four main cryptographic modules are hashlib, hmac, md5 & sha.
Let us understand this by an example. Everyone knows about ROT-13 cipher process in which character is replaced by the 13th character after that character. In the case where alphabets are getting over it is wrapping up. For an example P character is substituted by C character which is 13th character after P. For this there is a string library in python already which contains one very good function named “maketrans”. Basically to substitute one character for another is the main function of this character. So one can do below coding in order to encoding and decoding (Connor 2010).
So this is as easy as you think. All you need to call is right function and their method and it will be done in no time. Let us talk about real life scenario in which investigators do find PCF files which contains Base-64 encoding. One can code python program in order to find unallocated space of file in volatile memory itself. Python has inbuilt libraries and modules for decoding base64. It just takes 3 lines of code in order to do so as shown in below figure 2:
6.2 Metadata Extraction Along with File Information Using Python
Another good area to work with python is metadata extraction. There is no doubt that many cases in the past were solved with metadata information which contains much information ranging from various file types. File and metadata information is really helpful in forensics investigation. It can tell you that who was the author of particular file, when that file was created, when it was last modified and the location of last modified or files creation.
Such potential information can is really helpful to solve many cybercrime cases (Connor 2010). For an example
Let us talk about pdf files. Pypdf is a great python library which provides such information such as file splitting, file merging, file encryption etc... I am going to write only main lines of code by which whole program can be generated. First we need to import pyPdf module and then we need to call PdfFileReader object in that in order to make read all the files.
Another good area to work with python is metadata extraction. There is no doubt that many cases in the past were solved with metadata information which contains much information ranging from various file types. File and metadata information is really helpful in forensics investigation. It can tell you that who was the author of particular file, when that file was created, when it was last modified and the location of last modified or files creation.
Such potential information can is really helpful to solve many cybercrime cases (Connor 2010). For an example
Let us talk about pdf files. Pypdf is a great python library which provides such information such as file splitting, file merging, file encryption etc... I am going to write only main lines of code by which whole program can be generated. First we need to import pyPdf module and then we need to call PdfFileReader object in that in order to make read all the files.
After calling file this is the main coding by which we get the information about the pdf file. So you can clearly see that very small amount of code is used to get information from the pdf file. Thus how python helps in forensics information with its minimal code of implementation (Connor 2010).
6.3 Microsoft Windows Registry Analysis Using Python
Windows registry is very helpful area of Microsoft windows it stores all the configuration information of windows components. It does not only contain the information about locally stored software, but it also contains each and every information ranging wireless, networking, software & hardware. It depends on an analyst that how and what type of registry information he/she is looking for. Traditionally he/she can access this information by built in windows tools such as REGEDIT and REGEDIT32 (Connor 2010).
RunMRUkey is very interesting key in windows registry. It provides all last run commands through windows registry. If we want to build a python application in order to see the output of all last run command through this windows registry then its core mechanism should be like as follows:
Windows registry is very helpful area of Microsoft windows it stores all the configuration information of windows components. It does not only contain the information about locally stored software, but it also contains each and every information ranging wireless, networking, software & hardware. It depends on an analyst that how and what type of registry information he/she is looking for. Traditionally he/she can access this information by built in windows tools such as REGEDIT and REGEDIT32 (Connor 2010).
RunMRUkey is very interesting key in windows registry. It provides all last run commands through windows registry. If we want to build a python application in order to see the output of all last run command through this windows registry then its core mechanism should be like as follows:
So here you can also see that big piece of work is done in no time with simple lines of code in python.
6.4 Linux Artefacts Analysis Using Python
PyUTMP is another great python module. Basically the function of utmp file is to provide an information of the logged in users in Linux operating system. Information stored in utmp file is binary which cannot be read by traditional text editor that is why you need a specialized tool to read such information (Connor 2010).
Consider a scenario in which you have to perform a forensics investigation in Linux where you need to find the logged in users in august month of 2013 starting from 16th of august to end of the month. To perform such operation the python script should look like below. I am only showing core mechanism here. First we need to import time in python. Then below line should be appeared.
PyUTMP is another great python module. Basically the function of utmp file is to provide an information of the logged in users in Linux operating system. Information stored in utmp file is binary which cannot be read by traditional text editor that is why you need a specialized tool to read such information (Connor 2010).
Consider a scenario in which you have to perform a forensics investigation in Linux where you need to find the logged in users in august month of 2013 starting from 16th of august to end of the month. To perform such operation the python script should look like below. I am only showing core mechanism here. First we need to import time in python. Then below line should be appeared.
Then we have to define start time and end time as follows:
Once we have defined everything we have to implement the logic to get the list of logged in users among defined time and date. That logic should be as follows:
Thus how after this mechanism works, we just have to print our result. So here also you can see that how it’s easy to build quick small tools which can do really massive things for us in order to crack any forensics investigation case.
6.5 Other Areas of Forensics Investigation Using Python
So these were the common basic areas which are really helpful when any investigator conducts a forensics investigation. Apart from these areas there are many other areas in which python can be efficiently implemented in order to get quality output in no time.
6.5.1 Python to track web based email client
6.5 Other Areas of Forensics Investigation Using Python
So these were the common basic areas which are really helpful when any investigator conducts a forensics investigation. Apart from these areas there are many other areas in which python can be efficiently implemented in order to get quality output in no time.
6.5.1 Python to track web based email client
It is possible that you might phase a case in future where you need to find the credentials of any email account in order to investigate that case further. That account might contains hundreds of email in which you need to filter many mails to find the exact information which you are seeking for. Python contains many useful libraries which can help you to achieve your task easily (Connor 2010).
6.5.2 Decrypting Cipher Messages & Decoding Steganography
Up to here I have shown how to use various python libraries and how we can use them effectively to get much from it. However we are not fully depend on python libraries only. We can build python modules by yourself and can use it for later purpose. Zip-file module is very useful in case if any investigator wants to crack the password protection of any zip file (Connor 2010).
6.5.3 Volatility Analysis
To get the insight of system it is must that investigator must analyse the volatile RAM memory. It helps to analyse the open networks connections, passwords that are recently used & the whole process table. Next big challenge for this analysis is to carving sensitive useful information from volatile memory. Therefore volatility comes into the play which is one of the biggest open-source digital forensics projects. It provides framework for python library for getting output of various forensics artefacts.
7. Introduction to PE file & Format
In this section I am going to focus on PE file format. So that one can get better idea that why we are doing digital forensics in particular PE file format from many areas of computing world. PE file is nothing but portable executable file. It basically runs on 32 and 64 bit of operating system platform. PE file is a general category (Han, Keungi & Sangjin 2009). Specific format of PE files are *.exe, *.dll, *.obj & *.sys. Structure of PE file is shown in below figure:
6.5.2 Decrypting Cipher Messages & Decoding Steganography
Up to here I have shown how to use various python libraries and how we can use them effectively to get much from it. However we are not fully depend on python libraries only. We can build python modules by yourself and can use it for later purpose. Zip-file module is very useful in case if any investigator wants to crack the password protection of any zip file (Connor 2010).
6.5.3 Volatility Analysis
To get the insight of system it is must that investigator must analyse the volatile RAM memory. It helps to analyse the open networks connections, passwords that are recently used & the whole process table. Next big challenge for this analysis is to carving sensitive useful information from volatile memory. Therefore volatility comes into the play which is one of the biggest open-source digital forensics projects. It provides framework for python library for getting output of various forensics artefacts.
7. Introduction to PE file & Format
In this section I am going to focus on PE file format. So that one can get better idea that why we are doing digital forensics in particular PE file format from many areas of computing world. PE file is nothing but portable executable file. It basically runs on 32 and 64 bit of operating system platform. PE file is a general category (Han, Keungi & Sangjin 2009). Specific format of PE files are *.exe, *.dll, *.obj & *.sys. Structure of PE file is shown in below figure:
Any executable file starts with simple dos header which is also called as MS-DOS stub sometimes which is shown in above figure. Basically this is used to help program for dos execution along with the compatibility. Second part of this structure is image_nt_header. This is basically a unique identifier. It has various things in it such as various different sections, executable system, value of the time, and the property of the execution. After that data sections comes into the play which deals with many information such as debug data, various resources, coding and the raw data. Last but not the least section data part comes which involves other data such as execution program for the real execution of the program and the raw data along with other resources.
8. Packed PE File Format
Packed PE files are a compressed pe file. Once you have your executable file, you have to do packing of it means you need to compress that file. At the time of execution that file will be decompressed and it will be executed on the system. Sometimes packing is also known as “executing the compression”. Main benefit of packing is to protect the executable file. Protection is needed against some attacks known as “reverse engineering” in which attacker try to analyse the whole executable file and he tries to bypass the trial limit mechanism or purchase product mechanism.
By doing that type of activity he may able to access the full product without buying it forever. So against these types of attacks, packing/compression technique is used to protect the execution file.
9. Flowchart for the PE file Detection
Previously I have shared knowledge of pe file and their characteristics and attributes. From my previous sharing characteristics of the pe file can be defined as follows:
• PE file is compressed along with encryption.
• It is normal PE file which has a characteristics of packing.
There are common two detection methodologies exists in the world mentioned below based on the given categories of PE file mentioned above.
• Detection using entropy.
• Detection based on unpacking characteristics.
Any compressed and encrypted packed file’s data entropy will be always high compare to other traditional ones. Entropy in the entry point is the only one major thing which distinguishes packed PE file and normal PE file. Ideally the file whose entropy is higher than 6.85 is considered as a packed PE file. It is because the entropy section range in a normal PE file is 4 to 5. However 6.85 is more than this normal range so we can consider it as a packed PE file or packed encrypted PE file. There are many important properties of packed PE file such as READ, CODE, and EXECUTE, DATA & WRITE. However among all, WRITE is an essential property of packed PE file. Initial selection of packed PE file does base on the entry point which includes WRITE property within it (Han, Keungi & Sangjin 2009).
Based on this above theory, detection low chart of packed pe file should be somewhat like as follows:
8. Packed PE File Format
Packed PE files are a compressed pe file. Once you have your executable file, you have to do packing of it means you need to compress that file. At the time of execution that file will be decompressed and it will be executed on the system. Sometimes packing is also known as “executing the compression”. Main benefit of packing is to protect the executable file. Protection is needed against some attacks known as “reverse engineering” in which attacker try to analyse the whole executable file and he tries to bypass the trial limit mechanism or purchase product mechanism.
By doing that type of activity he may able to access the full product without buying it forever. So against these types of attacks, packing/compression technique is used to protect the execution file.
9. Flowchart for the PE file Detection
Previously I have shared knowledge of pe file and their characteristics and attributes. From my previous sharing characteristics of the pe file can be defined as follows:
• PE file is compressed along with encryption.
• It is normal PE file which has a characteristics of packing.
There are common two detection methodologies exists in the world mentioned below based on the given categories of PE file mentioned above.
• Detection using entropy.
• Detection based on unpacking characteristics.
Any compressed and encrypted packed file’s data entropy will be always high compare to other traditional ones. Entropy in the entry point is the only one major thing which distinguishes packed PE file and normal PE file. Ideally the file whose entropy is higher than 6.85 is considered as a packed PE file. It is because the entropy section range in a normal PE file is 4 to 5. However 6.85 is more than this normal range so we can consider it as a packed PE file or packed encrypted PE file. There are many important properties of packed PE file such as READ, CODE, and EXECUTE, DATA & WRITE. However among all, WRITE is an essential property of packed PE file. Initial selection of packed PE file does base on the entry point which includes WRITE property within it (Han, Keungi & Sangjin 2009).
Based on this above theory, detection low chart of packed pe file should be somewhat like as follows:
Detection of packed PE file firstly starts with the directory which can be any hard disk drive. From the receiving location, it finds the lower directory files in sequential format. Then it checks for various PE signatures. If it finds that then it does further analysis of section and entry point checking. Then as I have mentioned earlier, after getting entry point list, it distinguish packed pe file by finding if any entry point has WRITE property or not. Finally it calculates the entry of that particular section and tries to compare with the standard value which is 6. 6 is a pre-defined threshold value of entry for packed PE files. This method is the only effective method by which you can distinguish pe file and packed pe file in no time.
10. PE Analysis from Security Point of View
There are many typical items out there in PE file format which are dos header, MS dos stub, symbol table, pe file signature, file header, section table etc.. Now in this section I am going to describe each and every typical items in brief.
10. PE Analysis from Security Point of View
There are many typical items out there in PE file format which are dos header, MS dos stub, symbol table, pe file signature, file header, section table etc.. Now in this section I am going to describe each and every typical items in brief.
10.1 Dos Header – It is generally located at the very beginning of the PE file. It is a single recorded data. Loader program uses it’s information. To understand this, let us take an example. A pe signature portion which is going to be display later in the pe file is recorded via it’s offset at the very beginning in the dos header (Tevis & Hamilton). If we do not find any information in dos header it means our chances are high for detecting security flaws in it.
10.2 Dos Stub – As soon as dos header’s part is finished, dos stub is right after it following it. In the past when PC software ran in the MS-DOS OS, it holdover since that days. That particular program requires graphical user interface to run unless and if Portable executable file is invoked via MS Dos OS. Otherwise MS Dos will flash the message stating that particular program cannot run in DOS mode. Suddenly after that program gets terminated (Tevis & Hamilton).
10.3 File Header – After PE signature portion, file header comes. To understand let me explain that PE signature is nothing but simple involves those simple letters stated “PE”. Main function of file header is, to revel information about the environment in which the file is going to be operated. It might expect the characteristics of that file along with the content of the file. It also revels many information such as starting location of the symbol table, number of sections in that particular file, various symbols in the symbol table & the size of the variable length header.
This table follows symbol table directly, that is why it also revels the information about string table’s starting location (Tevis & Hamilton).
10.4 Optional Header – This table follows the file header. Starting of the option header is following the end of its last file header table. Misleading is the real name of the optional header that is used mostly in object code. This thing is mandatory in PE file format. There is fixed record of size in whole option header except it’s last field within it. This header revels more information about the data field than the data filed in the file header. Last field of any optional header is called as data directory. It is nothing but the variable length of list of the various records. Each records within that involve the starting location and the size of its data table which is generally located in the file (Tevis & Hamilton).
10.5 Section Table – As usual this is a sequential process. Starting of the section table follows the end of any optional header. It also contains more information of fixed size of records with data on the starting location, characteristics and the size in a PE file. There are specific values assigned for each entry in the section table which is used for specific sections in file header. Section entries are formed in such a way that they appear in PE file (Tevis & Hamilton).
10.6 Symbol Table - The size and area of the image table are focused around two fields in the document header that show this data. If the quality in the Number of Symbols field is zero, then the document holds no image table. The linker utilizes the image table within an item code document, yet the table is not needed in a PE record. The table is just present there for the utilization by a debugger. The image table holds the name of each information thing and capacity pronounced by the system and by any library or runtime environment code connected in with the project. Depending on which linker is utilized, the image table likewise holds the names of source code documents for the system. An inquiry of the capacity names in the image table could be utilized to identify a cushion flood security weakness in a system. Each capacity name recorded in the image table might be contrasted with a rundown of standard C library capacities powerless to cushion floods.
The ensuing matching entrances uncover powerless capacities that were either utilized within the requisition source code or were infused into the item code by the compiler throughout source code interpretation.
10.7 String Table - The string table is placed promptly emulating the image table. If an image table is not show in the document, then the string table is spotted where the image table might have begun. If the begin area of the image table field in the document header is zero, then the record does not hold a string table. The linker needs a string table in an item code record, yet the table is not needed in a PE document. As with the image table, the string table is just present there for utilization by a debugger. The string table holds the name of each variable name and area name that shows up in a project or in any library or runtime environment code connected in with the system. The segment table and image table just hold section names up to eight bytes long. For a name of any more stupendous length, a counterbalance is put away in the name field. This counterbalance focuses to the begin of a character string in the string table (Tevis & Hamilton).
10.8 Other Various Sections - The segments alluded to in the area table finish the rest of a PE document's substance. Some linkers put every discretionary table in its area. For instance, the fare table may be in the ".edata" segment. Other linkers put the discretionary table amidst other information in a segment. For instance, the import table may be in the ".text" area. The genuine executable code and steady information we generally take up with an executable document are put away in one or more areas. These areas are typically alluded to, individually, as the ".data" and ".text" segments, despite the fact that these may have different names (Tevis & Hamilton).
10.9 Import Table - The area of the import table in a PE record is found by ascertaining the document balance of the beginning area. This is carried out utilizing the Relative Virtual Address field in the information registry of the discretionary header and the Virtual Address and Pointer to Raw Data fields in the segment table. The import table holds the names of the element join library (DLL) documents and the capacities in those records that the project requires with a specific end goal to run. If a system does not utilize any DLL documents, then the import table is not show.
As I portrayed prior concerning the image table, the import table additionally holds the names of capacities utilized as a part of the record, yet just capacities foreign made from Dlls. This data could be utilized to focus a support flood security powerlessness in a document like the strategy utilized with the image table.
Note that if a record utilizes no Dlls and likewise holds no image table, then a quest for the names of defenceless capacities will think of an unfilled rundown. This ought not be viewed as an evidence that the system utilizes no defenceless capacities. Instead, it ought to call attention to the absence of enough data to make such a determination (Tevis & Hamilton).
In spite of the fact that the utilization of a particular DLL by a project does not, in itself, constitute a security helplessness, a security investigator may be intrigued by thinking about the Dlls utilized by a record. Looking at the reason or capacity served by a DLL may uncover operations performed by the program that aren't promptly evident from the client interface or programming documentation. This could incorporate Dlls to support in system associations, encryption, or establishment of records.
10.10 Export Table - The area of the fare table in a PE document is found by figuring the record balance of the beginning area as was portrayed above for the import table. The fare table holds the name of each one capacity in the document that is accessible for utilization by an alternate project. This is the typical conduct for a DLL; therefore, a fare table is normally not found in different sorts of PE records (Tevis & Hamilton).
11. Introduction to PEextract Tool
In this project, first of all I will be giving the importance of python scripting language, that’s what it is so much useful and flexible in order to be used in the forensics department. Later I explained which are the different areas of investigation for which one can develop tools in python scripting language. I am going to develop a small but handy and comprehensive tool named “PEextract” during my dissertation. This tool .This tool is created to analyse specifically PE files of packed executable. This tool will have many features such as hashing analysis; PE file attributes analysis, version information and metadata, section analyser. Not only this, but, my tool will also show which are the *.dll files and API functions imported within any packed executable file. It will have an ability to dump all the data in the output.
It will also analyses all the strings, file names and URLs within the executable file. Thus, how my tool has many robust features in it.
12. Implementation
12.1 SDLC Life Cycle - To create my artefact I am going to use SDLC methodology. SDLC is a life cycle of software development. Below figure shows all phases of the SDLC life cycle.
12. Implementation
12.1 SDLC Life Cycle - To create my artefact I am going to use SDLC methodology. SDLC is a life cycle of software development. Below figure shows all phases of the SDLC life cycle.
12.2 Requirement Analysis: In order to create my desired artefact, I have analysed what I will need during my artefact development. Below I have mentioned one python file which I am going to use throughout my development.
PEfile: It is a multi-platform module of python, which has an ability to read and work with the PE formats also known as portable executable format. It needs a very basic understanding of the PE file’s layout.
PEfile: It is a multi-platform module of python, which has an ability to read and work with the PE formats also known as portable executable format. It needs a very basic understanding of the PE file’s layout.
Structure of PEextract
Apart from this PEfile, I will be using some default python libraries in my code.
12.3 Design: As this tool is a command-line tool. There is no any design phase in my artefact. However to make it professional I have implemented logo by just default print command. Finally a layout of my tool is ready and it looks like below figure exactly.
12.3 Design: As this tool is a command-line tool. There is no any design phase in my artefact. However to make it professional I have implemented logo by just default print command. Finally a layout of my tool is ready and it looks like below figure exactly.
12.4 Implementation: This phase of this life cycle is very essential in which I will be implementing python code to develop my artefact. As this is a very initial phase. So 10% of artefact is ready now.
12.4.1 Tool Help - Firstly, I have provided help by which unknown user of this tool can come and know what does this tool does actually. For that I have provided below code. For this I am defining a function named HELP by def()(Python 3.3.5 documentation).
12.4.1 Tool Help - Firstly, I have provided help by which unknown user of this tool can come and know what does this tool does actually. For that I have provided below code. For this I am defining a function named HELP by def()(Python 3.3.5 documentation).
Now to test this code we need to give a simple command as below:
Command:
Command:
After giving this command you will the exact same output shown above.
12.4.2 HASH Calculation - Secondly, I implemented hash calculation for any PE files. Using this code, one can calculate the hash of that portable executable file. It helps to check whether the PE file has been modified or not. If modified, then the hash value will be different than previously calculated. A hash function is a function that takes data of a variable length succession of bytes and believers it to a fixed length arrangement. It is a restricted function. This methods if f is the hashing function, computing f(x) is really fast and straightforward, however attempting to get x again will take years. The worth returned by a hash function is often called a hash, message summary, hash quality, or checksum.
More often than not a hash function will prepare novel yield for a given information. However relying upon the calculation, there is a plausibility to find an impact because of the scientific hypothesis behind these functions(Python 3.3.5 documentation).
12.4.2 HASH Calculation - Secondly, I implemented hash calculation for any PE files. Using this code, one can calculate the hash of that portable executable file. It helps to check whether the PE file has been modified or not. If modified, then the hash value will be different than previously calculated. A hash function is a function that takes data of a variable length succession of bytes and believers it to a fixed length arrangement. It is a restricted function. This methods if f is the hashing function, computing f(x) is really fast and straightforward, however attempting to get x again will take years. The worth returned by a hash function is often called a hash, message summary, hash quality, or checksum.
More often than not a hash function will prepare novel yield for a given information. However relying upon the calculation, there is a plausibility to find an impact because of the scientific hypothesis behind these functions(Python 3.3.5 documentation).
I need to make clear that hash capacities are not a cryptographic convention, they don't encode or unscramble data, yet they are an essential some piece of numerous cryptographic conventions and apparatuses.
Probably the most utilized hash capacities are:
Probably the most utilized hash capacities are:
Md5: Message digest calculation transforming a 128 bit hash esteem. This is broadly used to check information uprightness. It is not suitable for utilization in different fields because of the security vulnerabilities of Md5.
SHA: Group of calculations composed by the U.s' NSA that are some piece of the U.s Federal Information preparing standard. These calculations are utilized generally within a few cryptographic requisitions. The message length ranges from 160 bits to 512 bits (Torres 2013).
The hashlib module, included in The Python Standard library is a module holding an interface to the most prominent hashing calculations. hashlib actualizes a portion of the calculations, however in the event that you have Openssl introduced, hashlib can utilize this calculations too.
Scripting to calculate hash is as follows:
The hashlib module, included in The Python Standard library is a module holding an interface to the most prominent hashing calculations. hashlib actualizes a portion of the calculations, however in the event that you have Openssl introduced, hashlib can utilize this calculations too.
Scripting to calculate hash is as follows:
Now let’s calculate hash with “- -hash” option. I am using ccsetup411.exe file which is an open source windows OS tweaking tool. The command is as follows:
Command:
Command:
Output:
As you can see it provides hexadecimal digits hash calculation of that exe file.
12.4.3 PEid Information - PEid identifies most regular packers, cryptors and compilers for PE records. It can as of now identify more than 450+ separate marks in PE records. Below is the code to detect the PE signatures in my tool(Python 3.3.5 documentation).
12.4.3 PEid Information - PEid identifies most regular packers, cryptors and compilers for PE records. It can as of now identify more than 450+ separate marks in PE records. Below is the code to detect the PE signatures in my tool(Python 3.3.5 documentation).
As if now there is no PE signature information available in my exe file which I created. So it is showing None.
12.4.4 File Information & Metadata - In Digital Forensics, the recuperated information needs to be appropriately archived. As beforehand said prior in the article, the information that is examined holds data about "Metadata".
The Digital Forensics industry benchmarks require ensured workstation analysts or crime scene investigation specialists to take after specific conventions throughout their examinations.
The principle goal of an appropriately led examination or investigation of a workstation or computerized media by an expert analyst is to find conceivable proof by method for seizure, pursuit, and recovery, while keeping up "information uprightness" of the first or suspect media. This confirmation must be capable be maintained in a Court of Law. A great practice might be to perform a hash of the 'suspect media' before starting any examination. A forensically clean duplicate (cleaned duplicate) of the suspect media ought to be made bit for bit. This is known as the "Proof media"(Moss). Once the examination is finished, an alternate hash is then performed against the proof media to guarantee an accurate match with the suspect media still exists.
The confirmation's metadata is greatly critical as it displays prove as to:
• The day file was created
• The day file was deleted
• The day file was last modified
• The time on which file was created, deleted and modified
• Computer username
• Etc..
Information can come in numerous structures, for example, database documents, record records, spread sheet documents, picture or media records, email and talk records, and provisional web records (from programs). The business and free scientific devices recorded later in this article, are simply a couple of the apparatuses that most advanced measurable experts like myself utilization to complete metadata investigation throughout their examinations.
To find these relevant information, the scripting(Guelfoweb 2014)
of my tool is as follows:
12.4.4 File Information & Metadata - In Digital Forensics, the recuperated information needs to be appropriately archived. As beforehand said prior in the article, the information that is examined holds data about "Metadata".
The Digital Forensics industry benchmarks require ensured workstation analysts or crime scene investigation specialists to take after specific conventions throughout their examinations.
The principle goal of an appropriately led examination or investigation of a workstation or computerized media by an expert analyst is to find conceivable proof by method for seizure, pursuit, and recovery, while keeping up "information uprightness" of the first or suspect media. This confirmation must be capable be maintained in a Court of Law. A great practice might be to perform a hash of the 'suspect media' before starting any examination. A forensically clean duplicate (cleaned duplicate) of the suspect media ought to be made bit for bit. This is known as the "Proof media"(Moss). Once the examination is finished, an alternate hash is then performed against the proof media to guarantee an accurate match with the suspect media still exists.
The confirmation's metadata is greatly critical as it displays prove as to:
• The day file was created
• The day file was deleted
• The day file was last modified
• The time on which file was created, deleted and modified
• Computer username
• Etc..
Information can come in numerous structures, for example, database documents, record records, spread sheet documents, picture or media records, email and talk records, and provisional web records (from programs). The business and free scientific devices recorded later in this article, are simply a couple of the apparatuses that most advanced measurable experts like myself utilization to complete metadata investigation throughout their examinations.
To find these relevant information, the scripting(Guelfoweb 2014)
of my tool is as follows:
To use this feature command is as follows:
Command:
Command:
Output:
Command:
Output:
Thus how we are manage to get the metadata information with just simple script with Python.
12.4.5 Section Analysis - A PE document segment speaks to code or information or something to that affect. While code is simply code, there are various sorts of information. Furthermore read/write program information, different sorts of information in areas incorporate API import and fare tables, assets, and migrations. Each one segment has its own particular set of in-memory traits, including whether the area holds code, whether its read-only or read/write, and whether the information in the area is imparted between all methodologies utilizing the executable(Miscellaneous operating system interfaces).
Generally talking, all the code or information in a segment is legitimately related somehow. At the very least, there are for the most part no less than two areas in a PE document: one for code, the other for information. Commonly, there's no less than one other kind of information segment in a PE record. I'll take a gander at the different sorts of areas in Part 2 of this article one month from now.
Each segment has a different name. This name is proposed to pass on the motivation behind the segment. For instance, a segment called .rdata shows a read-only information area. Area names are utilized exclusively for the profit of people, and are inconsequential to the working framework. An area named FOOBAR is almost as substantial as a segment called .content. Microsoft normally prefixes their area names with a period, however it’s not a prerequisite. For quite some time, the Borland linker utilized segment names like CODE and DATA. Once mapped into memory, areas dependably begin on at any rate a page limit. That is, the point at which a PE segment is mapped into memory, the first byte of each one area compares to a memory page. On x86 CPU, pages are 4kb adjusted, while on the IA-64, they're 8kb adjusted. The accompanying code indicates a bit of PEDUMP yield for the .text and .data segment of the Windows XP Kernel32.dll.
12.4.5 Section Analysis - A PE document segment speaks to code or information or something to that affect. While code is simply code, there are various sorts of information. Furthermore read/write program information, different sorts of information in areas incorporate API import and fare tables, assets, and migrations. Each one segment has its own particular set of in-memory traits, including whether the area holds code, whether its read-only or read/write, and whether the information in the area is imparted between all methodologies utilizing the executable(Miscellaneous operating system interfaces).
Generally talking, all the code or information in a segment is legitimately related somehow. At the very least, there are for the most part no less than two areas in a PE document: one for code, the other for information. Commonly, there's no less than one other kind of information segment in a PE record. I'll take a gander at the different sorts of areas in Part 2 of this article one month from now.
Each segment has a different name. This name is proposed to pass on the motivation behind the segment. For instance, a segment called .rdata shows a read-only information area. Area names are utilized exclusively for the profit of people, and are inconsequential to the working framework. An area named FOOBAR is almost as substantial as a segment called .content. Microsoft normally prefixes their area names with a period, however it’s not a prerequisite. For quite some time, the Borland linker utilized segment names like CODE and DATA. Once mapped into memory, areas dependably begin on at any rate a page limit. That is, the point at which a PE segment is mapped into memory, the first byte of each one area compares to a memory page. On x86 CPU, pages are 4kb adjusted, while on the IA-64, they're 8kb adjusted. The accompanying code indicates a bit of PEDUMP yield for the .text and .data segment of the Windows XP Kernel32.dll.
Example of Sections are as follows:
###################################################
.ndata 0x73000 0x2f1000 0 YES
MD5 hash: d41d8cd98f00b204e9800998ecf8427e
SHA-1 hash: da39a3ee5e6b4b0d3255bfef95601890afd80709
.rsrc 0x364000 0x7a68 31744 NO
MD5 hash: 2f2e06532cfb2c4423efdd21d0eb02e8
###################################################
Now it is time to use this feature in my artefact. Command for that is shown below.
Command:
Output:
12.4.6 Various Imported Dll files and API functions – As you all know that packed EXE file contains many dll files which is known as dynamic linking library. Each dll files contains some API functions. This part of code checks for all those API functions which are suspicious and they are being called by those malicious dll files. So this is the main function of this code(Kevin, M & F).
Command to execute this script is written below.
Command:
Command:
Output:
12.4.7 Malicious API Analysis – Over the past a few years, element code investigation has ended up being a successful weapon in the battle against code infusion ambushes. In any case, permitting shell code to proceed with its execution and legitimately handle its arrangement of Windows API calls is a troublesome errand for element code analysers, predominantly because of the way that the code runs in a re-enacted nature. The libemu element code analyser, for instance, stacks an altered set of Dlls to their default burden addresses in memory and keeps up a static rundown of Windows API call addresses that it re-enacts when the API location is stacked from inside the guideline emulator. Shell OS takes a comparative methodology to libemu in that it recreates an altered set API calls, yet contrasts in that API calls are snared by page-level memory traps (see the dialog in or the idea of stealth breakpoints in for a nitty gritty outline), as opposed to contrasting the PC with the set of mimicked API call addresses at each one single-stepped guideline. In any case, the actuality remains that element code dissection devices can't undoubtedly help the re-enactment of the horde of Windows API calls accessible, and extra outsider Dlls are frequently stacked by the requisition being investigated.
It is not phenomenal, for instance, that in excess of 2530,000 DLL capacities are available in memory at whenever. This is why it is so important to check all api functions within an executable file. Code for this feature is as below:
It is not phenomenal, for instance, that in excess of 2530,000 DLL capacities are available in memory at whenever. This is why it is so important to check all api functions within an executable file. Code for this feature is as below:
Below command shows how to run --apialert option in my tool in order to analyse the suspicious api functions.
Command:
Command:
Output:
12.4.8 Malicious URL Analysis – Did you ever mark that you install an antivirus software and many time it gives an alert or popup that, new updates are available kindly install them to protect against the virus attacks. Because when you installed that software through an exe file, it also stores URL collection in our local machine through which it goes to those URL backend and checks if there are new updates available or not. So the point is that it also happens in the malware execution case as well. Let us assume that any malware got installed on the local machine. However except its own capability it uses many websites form internet where it download other supporting files in order to successful execution. Here in this part I have done URL checking coding through which one can extract all URL list form any packed PE file. So it also helps in digital forensics to solve the cases. Sometime we might get the information of an actual author from URL where the malicious file is being executed. Below is the code to pull the all url list form any packed PE file.
Command:
Output:
12.4.9 String Analysis – A string in a project is an arrangement of characters, for example, "ball." A system holds strings in the event that it prints a message, unites with a URL, or duplicates a record to a particular area. Looking through the strings might be a straightforward approach to get implies about the usefulness of a system. Case in point, if the project gets to a URL, then you will see the URL got to, put away as a string in the system. You can utilize the Strings project, to hunt an executable down strings, which are normally put away in either ASCII or Unicode form. At the point when Strings scan an executable for ASCII and Unicode strings, it overlooks the connection and designing, with the goal that it can dissect any document sort and identify strings over a whole record. Strings hunt down a three-letter or more amazing arrangement of ASCII and Unicode characters, took after by a string end character(Sikorski & Honig).
It is stated in the history that many hackers try to reverse engineer the application in order to get the full access of the software. They use this string analysis technique in order to find from where loop is running and on which point it is jumping. That is why I have decided to include this feature in my tool. Command for the string analysis is shown below:
Command:
Output:
Now and again the strings distinguished by the Strings project are not real strings. For instance, if Strings discovers the arrangement of bytes 0x56, 0x50, 0x33, 0x00, it will decipher that as the string Vp3. At the same time those bytes may not really speak to that string; they could be a memory address, CPU guidelines, or information utilized by the system. Strings surrenders it over to the client to channel out the invalid strings(Sikorski & Honig).
So this is how we can do string analysis for packed PE files. It can give you much information than another feature of my tool.
12.4.10 Dumping Import & Export Instances – The Portable Executable record arrange, the arrangement utilized for executable within such situations as OS/2 and Win32, is honestly overall recorded by Microsoft, however what isn't decently reported is the thing that the working framework does with the substance of the document when really stacking an executable. In this content I will allude to the piece of the working framework that heaps the executable as the PE loader or simply essentially the loader. PE records are not restricted to .exe documents, Vxds and Dlls are different sorts of PE documents, however in this content I will be centring on. Excel documents and.dll documents, which don't fundamentally need to have those document amplifications. The real structures that show up in the records are characterized in winnt. Hand are utilized all around this content. It is accepted that the onlooker is as of now acquainted with the general structure of PE documents. At the point when an executable (this incorporates Dlls) is stacked into memory, it is not essentially duplicated into memory and executed, there are various steps the working framework takes to load the picture rightly and set up things in that memory picture before it bounced to the code in that picture(Portable executable loaders and wrappers). Code to find import and export entry is as follows:
Command:
Output:
Command:
Output:
13. Evaluation & Testing
13.1 Testing with auto option - I have already demonstrated each and every part very precisely in the 3rd chapter of this draft. Here I am going to use the last feature of my tool which is an auto option. If we select –auto or –a option then it will use each and every feature of the tool and will give very long and comprehensive analysis. For testing purpose I am disabling string analysis. Reason behind this is, it generates very long output when we use string analysis. So I am disabling that feature and except that I am using every feature by selecting a single option named --auto or –a. So to use these feature command is this.
Command 1:
13.1 Testing with auto option - I have already demonstrated each and every part very precisely in the 3rd chapter of this draft. Here I am going to use the last feature of my tool which is an auto option. If we select –auto or –a option then it will use each and every feature of the tool and will give very long and comprehensive analysis. For testing purpose I am disabling string analysis. Reason behind this is, it generates very long output when we use string analysis. So I am disabling that feature and except that I am using every feature by selecting a single option named --auto or –a. So to use these feature command is this.
Command 1:
Command 2:
Output:
=========================================================================================
___ ___ _ _ _____ _
// ( _`\ ( _`\ ( )_ ( )_ (_ _) (_ )
// | |_) )| (_(_) __ | ,_) _ __ _ _ ___ | ,_) | | _ _ | |
// | ,__/ | _)_ / __ \(`\/ )| | ( __)/ _ ) / ___)| | | | / _`\ /'_`\ | |
// | | | (_( )( ___/ > < | |_ | | ( (_| |( (___ | |_ | |( (_) )( (_) ) | |
// (_) (____/ \____)(_/\_)`\__)(_) `\__,_)`\____)`\__) (_)`\___/ \___/'(___)
//
//
=========================================================================================
[1] PEFILE ATTRIBUTES
Exe_Name: master malware.exe
Exe_Size: 1264795 Bytes
Total_Sections: 5
Any_DLLs: False
Compilation_Time: 2009-07-03 04:31:54
=========================================================================================>
[2] HASH CALCUALTION
MD5 & SHA1 HASH VALUES ARE AS FOLLOWS:
SHA-1 : 98dfbc07fe3c295732111bcf787eaf58ecc75dcc
MD5 : 2bd10332ae061482d5d505314a97b40c
=========================================================================================>
[3] PEID INFORMATION
No Packer Information Available.
=========================================================================================>
[4] METADATA INFORMATION
=========================================================================================>
[5] DIFFERENT SECTION INFORMATION WITHIN EXECUTABLE
Number of Sections: 5
Section VirtualAddress VirtualSize SizeofRawData Suspicious
.text 0x1000 0x1066e 67584 NO
MD5 hash: ab290706f4b6bfa2b5883b3ee28b7347
SHA-1 hash: 0e9b64703c5afb4220e36fb41505b928ef6d2cb9
.rdata 0x12000 0x17d5 6144 NO
MD5 hash: 7e6bcefe52790da11cb917e2ed246c29
SHA-1 hash: 5660608794b2ccf2556c49c28c302fd718339605
.data 0x14000 0xbff4 512 NO
MD5 hash: 2821477811bfd11f4acd2c1da2aba6da
SHA-1 hash: f28af599dffabff91bb1c6fce831f020e4799fa8
.CRT 0x20000 0x10 512 YES
MD5 hash: 686666d109c1b7ad91d3938f41d2712a
SHA-1 hash: 2b4e8377002fe7fbfee868ec21b6f9e5937dfb22
.rsrc 0x21000 0x16b9c 93184 NO
MD5 hash: b2398684ad7a733c853c5a62e1271449
SHA-1 hash: 0a2547579ba5cb2f69a4fe48309bbe7ef64a8e2d
=========================================================================================>
[6] INFORMATION OF IMPORTED DLL AND API FUNCTIONS
[1] COMCTL32.dll
0x41202c None [2] KERNEL32.dll
0x412068 DeleteFileA
0x41206c DeleteFileW
0x412070 CreateDirectoryA
0x412074 CreateDirectoryW
0x412078 FindClose
0x41207c FindNextFileA
0x412080 FindFirstFileA
0x412084 FindNextFileW
0x412088 FindFirstFileW
0x41208c GetTickCount
0x412090 WideCharToMultiByte
0x412094 MultiByteToWideChar
0x412098 GetVersionExA
0x41209c GlobalAlloc
0x4120a0 lstrlenA
0x4120a4 GetModuleFileNameA
0x4120a8 FindResourceA
0x4120ac GetModuleHandleA
0x4120b0 HeapAlloc
0x4120b4 GetProcessHeap
0x4120b8 HeapFree
0x4120bc HeapReAlloc
0x4120c0 CompareStringA
0x4120c4 ExitProcess
0x4120c8 GetLocaleInfoA
0x4120cc GetNumberFormatA
0x4120d0 GetProcAddress
0x4120d4 DosDateTimeToFileTime
0x4120d8 GetDateFormatA
0x4120dc GetTimeFormatA
0x4120e0 FileTimeToSystemTime
0x4120e4 FileTimeToLocalFileTime
0x4120e8 ExpandEnvironmentStringsA
0x4120ec WaitForSingleObject
0x4120f0 SetCurrentDirectoryA
0x4120f4 Sleep
0x4120f8 GetTempPathA
0x4120fc MoveFileExA
0x412100 GetModuleFileNameW
0x412104 SetEnvironmentVariableA
0x412108 GetCommandLineA
0x41210c LocalFileTimeToFileTime
0x412110 SystemTimeToFileTime
0x412114 GetSystemTime
0x412118 IsDBCSLeadByte
0x41211c GetCPInfo
0x412120 FreeLibrary
0x412124 LoadLibraryA
0x412128 GetCurrentDirectoryA
0x41212c GetFullPathNameA
0x412130 SetFileAttributesW
0x412134 SetFileAttributesA
0x412138 GetFileAttributesW
0x41213c GetFileAttributesA
0x412140 WriteFile
0x412144 GetStdHandle
0x412148 ReadFile
0x41214c SetLastError
0x412150 CreateFileW
0x412154 CreateFileA
0x412158 GetFileType
0x41215c SetEndOfFile
0x412160 SetFilePointer
0x412164 MoveFileA
0x412168 SetFileTime
0x41216c GetCurrentProcess
0x412170 CloseHandle
0x412174 GetLastError
0x412178 lstrcmpiA[3] USER32.dll
0x4121ac ReleaseDC
0x4121b0 GetDC
0x4121b4 SendMessageA
0x4121b8 wsprintfA
0x4121bc SetDlgItemTextA
0x4121c0 EndDialog
0x4121c4 DestroyIcon
0x4121c8 SendDlgItemMessageA
0x4121cc GetDlgItemTextA
0x4121d0 DialogBoxParamA
0x4121d4 IsWindowVisible
0x4121d8 WaitForInputIdle
0x4121dc GetSysColor
0x4121e0 PostMessageA
0x4121e4 SetMenu
0x4121e8 SetFocus
0x4121ec LoadBitmapA
0x4121f0 LoadIconA
0x4121f4 CharToOemA
0x4121f8 OemToCharA
0x4121fc GetClassNameA
0x412200 CharUpperA
0x412204 GetWindowRect
0x412208 GetParent
0x41220c MapWindowPoints
0x412210 CreateWindowExA
0x412214 UpdateWindow
0x412218 SetWindowTextA
0x41221c LoadCursorA
0x412220 RegisterClassExA
0x412224 SetWindowLongA
0x412228 GetWindowLongA
0x41222c DefWindowProcA
0x412230 PeekMessageA
0x412234 GetMessageA
0x412238 DispatchMessageA
0x41223c DestroyWindow
0x412240 GetClientRect
0x412244 CopyRect
0x412248 IsWindow
0x41224c MessageBoxA
0x412250 ShowWindow
0x412254 GetDlgItem
0x412258 EnableWindow
0x41225c FindWindowExA
0x412260 wvsprintfA
0x412264 CharToOemBuffA
0x412268 LoadStringA
0x41226c SetWindowPos
0x412270 GetWindowTextA
0x412274 GetWindow
0x412278 GetSystemMetrics
0x41227c OemToCharBuffA
0x412280 TranslateMessage[4] GDI32.dll
0x412044 GetDeviceCaps
0x412048 GetObjectA
0x41204c CreateCompatibleBitmap
0x412050 SelectObject
0x412054 StretchBlt
0x412058 CreateCompatibleDC
0x41205c DeleteObject
0x412060 DeleteDC[5] COMDLG32.dll
0x412034 GetSaveFileNameA
0x412038 CommDlgExtendedError
0x41203c GetOpenFileNameA[6] ADVAPI32.dll
0x412000 LookupPrivilegeValueA
0x412004 RegOpenKeyExA
0x412008 RegQueryValueExA
0x41200c RegCreateKeyExA
0x412010 RegSetValueExA
0x412014 RegCloseKey
0x412018 SetFileSecurityW
0x41201c SetFileSecurityA
0x412020 OpenProcessToken
0x412024 AdjustTokenPrivileges[7] SHELL32.dll
0x412188 ShellExecuteExA
0x41218c SHFileOperationA
0x412190 SHGetFileInfoA
0x412194 SHGetSpecialFolderLocation
0x412198 SHGetMalloc
0x41219c SHBrowseForFolderA
0x4121a0 SHGetPathFromIDListA
0x4121a4 SHChangeNotify[8] ole32.dll
0x412288 CreateStreamOnHGlobal
0x41228c OleInitialize
0x412290 CoCreateInstance
0x412294 OleUninitialize
0x412298 CLSIDFromString[9] OLEAUT32.dll
0x412180 None
=========================================================================================>
[7] SUSPICIOUS API ALERT INFORMATION
Func. Name: CreateDirectoryA
Func. Name: CreateDirectoryW
Func. Name: CreateFileA
Func. Name: CreateFileW
Func. Name: DeleteFileA
Func. Name: DeleteFileW
Func. Name: FindFirstFileA
Func. Name: FindFirstFileW
Func. Name: FindNextFileA
Func. Name: FindNextFileW
Func. Name: FindResourceA
Func. Name: FindWindowExA
Func. Name: GetCommandLineA
Func. Name: GetFileAttributesA
Func. Name: GetFileAttributesW
Func. Name: GetModuleFileNameA
Func. Name: GetModuleFileNameW
Func. Name: GetModuleHandleA
Func. Name: GetProcAddress
Func. Name: GetTempPathA
Func. Name: GetTickCount
Func. Name: GetVersionExA
Func. Name: LoadLibraryA
Func. Name: OpenProcessToken
Func. Name: RegCloseKey
Func. Name: RegCreateKeyExA
Func. Name: RegOpenKeyExA
Func. Name: ShellExecuteExA
Func. Name: Sleep
Func. Name: WriteFile
=========================================================================================
[8] DUMPING ALL URLS FROM EXECUTABLE
FILE: %s.%d.tmp
FILE: ADVAPI32.dll
FILE: COMCTL32.DLL
FILE: COMCTL32.dll
FILE: COMDLG32.dll
FILE: GDI32.dll
FILE: KERNEL32.dll
FILE: OLEAUT32.dll
FILE: RC\accounts23.dat
FILE: RC\apaths23.dat
FILE: RC\bans23.dat
FILE: RC\console23.dat
FILE: RC\downlist23.dat
FILE: RC\dstats23.dat
FILE: RC\forwards23.dat
FILE: RC\liteserve.exe
FILE: RC\maildomains23.dat
FILE: RC\mimes.txt
FILE: RC\php\license.txt
FILE: RC\php\php.exe
FILE: RC\php\php4ts.dll
FILE: RC\scripts23.dat
FILE: RC\spaths23.dat
FILE: RC\supaths23.dat
FILE: RC\triggers23.dat
FILE: RC\uplist23.dat
FILE: RC\virtualpaths23.dat
FILE: RC\webdomains23.dat
FILE: SHELL32.dll
FILE: USER32.dll
FILE: liteserve.lnk
FILE: ole32.dll
FILE: riched20.dll
FILE: riched32.dll
FILE: server.lnk
FILE: shlwapi.dll
URL: RC\www\abortshutdown.php
URL: RC\www\askreboot.php
URL: RC\www\beep500.php
URL: RC\www\beep5000.php
URL: RC\www\beep50000.php
URL: RC\www\beep500000.php
URL: RC\www\capslock.php
URL: RC\www\closeall.php
URL: RC\www\closecd.php
URL: RC\www\emptybin.php
URL: RC\www\exitwin.php
URL: RC\www\force60.php
URL: RC\www\hibernate.php
URL: RC\www\hideall.php
URL: RC\www\hidedesktop.php
URL: RC\www\lock.php
URL: RC\www\logoff.php
URL: RC\www\message.php
URL: RC\www\minimize.php
URL: RC\www\monitor.php
URL: RC\www\monitor2.php
URL: RC\www\mouseright.php
URL: RC\www\mute.php
URL: RC\www\nircmd.exe
URL: RC\www\numlock.php
URL: RC\www\opencd.php
URL: RC\www\poweroff.php
URL: RC\www\question.php
URL: RC\www\question1.php
URL: RC\www\question2.php
URL: RC\www\reboot.php
URL: RC\www\resize.php
URL: RC\www\restartexplorer.php
URL: RC\www\screensaver.php
URL: RC\www\screensavertimeout.php
URL: RC\www\screensavertimeout2.php
URL: RC\www\screenshot.php
URL: RC\www\server.exe
URL: RC\www\showall.php
URL: RC\www\showdesktop.php
URL: RC\www\speak.php
URL: RC\www\speak1.php
URL: RC\www\speakfile.php
URL: RC\www\standby.php
URL: RC\www\stdbeep.php
URL: RC\www\stopscreenshot.php
URL: RC\www\transparent.php
URL: RC\www\transparent2.php
URL: RC\www\trayballoon.php
URL: RC\www\trayballoon2.php
URL: RC\www\trayballoon3.php
URL: RC\www\trayballoon4.php
URL: RC\www\volume.php
=========================================================================================
=========================================================================================
[10] IMPORT-EXPORT DATA INSTANCES
[IMAGE_IMPORT_DESCRIPTOR]
0x114DC 0x0 OriginalFirstThunk: 0x129D0
0x114DC 0x0 Characteristics: 0x129D0
0x114E0 0x4 TimeDateStamp: 0x0 [Thu Jan 1 00:00:00 1970 UTC]
0x114E4 0x8 ForwarderChain: 0x0
0x114E8 0xC Name: 0x12C44
0x114EC 0x10 FirstThunk: 0x1202C
[IMAGE_EXPORT_DIRECTORY]
0x12350 0x0 Characteristics: 0x0
0x12354 0x4 TimeDateStamp: 0x4A4DEC2A [Fri Jul 3 11:31:54 2009 UTC]
0x12358 0x8 MajorVersion: 0x0
0x1235A 0xA MinorVersion: 0x0
0x1235C 0xC Name: 0x13778
0x12360 0x10 Base: 0x1
0x12364 0x14 NumberOfFunctions: 0x0
0x12368 0x18 NumberOfNames: 0x0
0x1236C 0x1C AddressOfFunctions: 0x0
0x12370 0x20 AddressOfNames: 0x0
0x12374 0x24 AddressOfNameOrdinals: 0x0
___ ___ _ _ _____ _
// ( _`\ ( _`\ ( )_ ( )_ (_ _) (_ )
// | |_) )| (_(_) __ | ,_) _ __ _ _ ___ | ,_) | | _ _ | |
// | ,__/ | _)_ / __ \(`\/ )| | ( __)/ _ ) / ___)| | | | / _`\ /'_`\ | |
// | | | (_( )( ___/ > < | |_ | | ( (_| |( (___ | |_ | |( (_) )( (_) ) | |
// (_) (____/ \____)(_/\_)`\__)(_) `\__,_)`\____)`\__) (_)`\___/ \___/'(___)
//
//
=========================================================================================
[1] PEFILE ATTRIBUTES
Exe_Name: master malware.exe
Exe_Size: 1264795 Bytes
Total_Sections: 5
Any_DLLs: False
Compilation_Time: 2009-07-03 04:31:54
=========================================================================================>
[2] HASH CALCUALTION
MD5 & SHA1 HASH VALUES ARE AS FOLLOWS:
SHA-1 : 98dfbc07fe3c295732111bcf787eaf58ecc75dcc
MD5 : 2bd10332ae061482d5d505314a97b40c
=========================================================================================>
[3] PEID INFORMATION
No Packer Information Available.
=========================================================================================>
[4] METADATA INFORMATION
=========================================================================================>
[5] DIFFERENT SECTION INFORMATION WITHIN EXECUTABLE
Number of Sections: 5
Section VirtualAddress VirtualSize SizeofRawData Suspicious
.text 0x1000 0x1066e 67584 NO
MD5 hash: ab290706f4b6bfa2b5883b3ee28b7347
SHA-1 hash: 0e9b64703c5afb4220e36fb41505b928ef6d2cb9
.rdata 0x12000 0x17d5 6144 NO
MD5 hash: 7e6bcefe52790da11cb917e2ed246c29
SHA-1 hash: 5660608794b2ccf2556c49c28c302fd718339605
.data 0x14000 0xbff4 512 NO
MD5 hash: 2821477811bfd11f4acd2c1da2aba6da
SHA-1 hash: f28af599dffabff91bb1c6fce831f020e4799fa8
.CRT 0x20000 0x10 512 YES
MD5 hash: 686666d109c1b7ad91d3938f41d2712a
SHA-1 hash: 2b4e8377002fe7fbfee868ec21b6f9e5937dfb22
.rsrc 0x21000 0x16b9c 93184 NO
MD5 hash: b2398684ad7a733c853c5a62e1271449
SHA-1 hash: 0a2547579ba5cb2f69a4fe48309bbe7ef64a8e2d
=========================================================================================>
[6] INFORMATION OF IMPORTED DLL AND API FUNCTIONS
[1] COMCTL32.dll
0x41202c None [2] KERNEL32.dll
0x412068 DeleteFileA
0x41206c DeleteFileW
0x412070 CreateDirectoryA
0x412074 CreateDirectoryW
0x412078 FindClose
0x41207c FindNextFileA
0x412080 FindFirstFileA
0x412084 FindNextFileW
0x412088 FindFirstFileW
0x41208c GetTickCount
0x412090 WideCharToMultiByte
0x412094 MultiByteToWideChar
0x412098 GetVersionExA
0x41209c GlobalAlloc
0x4120a0 lstrlenA
0x4120a4 GetModuleFileNameA
0x4120a8 FindResourceA
0x4120ac GetModuleHandleA
0x4120b0 HeapAlloc
0x4120b4 GetProcessHeap
0x4120b8 HeapFree
0x4120bc HeapReAlloc
0x4120c0 CompareStringA
0x4120c4 ExitProcess
0x4120c8 GetLocaleInfoA
0x4120cc GetNumberFormatA
0x4120d0 GetProcAddress
0x4120d4 DosDateTimeToFileTime
0x4120d8 GetDateFormatA
0x4120dc GetTimeFormatA
0x4120e0 FileTimeToSystemTime
0x4120e4 FileTimeToLocalFileTime
0x4120e8 ExpandEnvironmentStringsA
0x4120ec WaitForSingleObject
0x4120f0 SetCurrentDirectoryA
0x4120f4 Sleep
0x4120f8 GetTempPathA
0x4120fc MoveFileExA
0x412100 GetModuleFileNameW
0x412104 SetEnvironmentVariableA
0x412108 GetCommandLineA
0x41210c LocalFileTimeToFileTime
0x412110 SystemTimeToFileTime
0x412114 GetSystemTime
0x412118 IsDBCSLeadByte
0x41211c GetCPInfo
0x412120 FreeLibrary
0x412124 LoadLibraryA
0x412128 GetCurrentDirectoryA
0x41212c GetFullPathNameA
0x412130 SetFileAttributesW
0x412134 SetFileAttributesA
0x412138 GetFileAttributesW
0x41213c GetFileAttributesA
0x412140 WriteFile
0x412144 GetStdHandle
0x412148 ReadFile
0x41214c SetLastError
0x412150 CreateFileW
0x412154 CreateFileA
0x412158 GetFileType
0x41215c SetEndOfFile
0x412160 SetFilePointer
0x412164 MoveFileA
0x412168 SetFileTime
0x41216c GetCurrentProcess
0x412170 CloseHandle
0x412174 GetLastError
0x412178 lstrcmpiA[3] USER32.dll
0x4121ac ReleaseDC
0x4121b0 GetDC
0x4121b4 SendMessageA
0x4121b8 wsprintfA
0x4121bc SetDlgItemTextA
0x4121c0 EndDialog
0x4121c4 DestroyIcon
0x4121c8 SendDlgItemMessageA
0x4121cc GetDlgItemTextA
0x4121d0 DialogBoxParamA
0x4121d4 IsWindowVisible
0x4121d8 WaitForInputIdle
0x4121dc GetSysColor
0x4121e0 PostMessageA
0x4121e4 SetMenu
0x4121e8 SetFocus
0x4121ec LoadBitmapA
0x4121f0 LoadIconA
0x4121f4 CharToOemA
0x4121f8 OemToCharA
0x4121fc GetClassNameA
0x412200 CharUpperA
0x412204 GetWindowRect
0x412208 GetParent
0x41220c MapWindowPoints
0x412210 CreateWindowExA
0x412214 UpdateWindow
0x412218 SetWindowTextA
0x41221c LoadCursorA
0x412220 RegisterClassExA
0x412224 SetWindowLongA
0x412228 GetWindowLongA
0x41222c DefWindowProcA
0x412230 PeekMessageA
0x412234 GetMessageA
0x412238 DispatchMessageA
0x41223c DestroyWindow
0x412240 GetClientRect
0x412244 CopyRect
0x412248 IsWindow
0x41224c MessageBoxA
0x412250 ShowWindow
0x412254 GetDlgItem
0x412258 EnableWindow
0x41225c FindWindowExA
0x412260 wvsprintfA
0x412264 CharToOemBuffA
0x412268 LoadStringA
0x41226c SetWindowPos
0x412270 GetWindowTextA
0x412274 GetWindow
0x412278 GetSystemMetrics
0x41227c OemToCharBuffA
0x412280 TranslateMessage[4] GDI32.dll
0x412044 GetDeviceCaps
0x412048 GetObjectA
0x41204c CreateCompatibleBitmap
0x412050 SelectObject
0x412054 StretchBlt
0x412058 CreateCompatibleDC
0x41205c DeleteObject
0x412060 DeleteDC[5] COMDLG32.dll
0x412034 GetSaveFileNameA
0x412038 CommDlgExtendedError
0x41203c GetOpenFileNameA[6] ADVAPI32.dll
0x412000 LookupPrivilegeValueA
0x412004 RegOpenKeyExA
0x412008 RegQueryValueExA
0x41200c RegCreateKeyExA
0x412010 RegSetValueExA
0x412014 RegCloseKey
0x412018 SetFileSecurityW
0x41201c SetFileSecurityA
0x412020 OpenProcessToken
0x412024 AdjustTokenPrivileges[7] SHELL32.dll
0x412188 ShellExecuteExA
0x41218c SHFileOperationA
0x412190 SHGetFileInfoA
0x412194 SHGetSpecialFolderLocation
0x412198 SHGetMalloc
0x41219c SHBrowseForFolderA
0x4121a0 SHGetPathFromIDListA
0x4121a4 SHChangeNotify[8] ole32.dll
0x412288 CreateStreamOnHGlobal
0x41228c OleInitialize
0x412290 CoCreateInstance
0x412294 OleUninitialize
0x412298 CLSIDFromString[9] OLEAUT32.dll
0x412180 None
=========================================================================================>
[7] SUSPICIOUS API ALERT INFORMATION
Func. Name: CreateDirectoryA
Func. Name: CreateDirectoryW
Func. Name: CreateFileA
Func. Name: CreateFileW
Func. Name: DeleteFileA
Func. Name: DeleteFileW
Func. Name: FindFirstFileA
Func. Name: FindFirstFileW
Func. Name: FindNextFileA
Func. Name: FindNextFileW
Func. Name: FindResourceA
Func. Name: FindWindowExA
Func. Name: GetCommandLineA
Func. Name: GetFileAttributesA
Func. Name: GetFileAttributesW
Func. Name: GetModuleFileNameA
Func. Name: GetModuleFileNameW
Func. Name: GetModuleHandleA
Func. Name: GetProcAddress
Func. Name: GetTempPathA
Func. Name: GetTickCount
Func. Name: GetVersionExA
Func. Name: LoadLibraryA
Func. Name: OpenProcessToken
Func. Name: RegCloseKey
Func. Name: RegCreateKeyExA
Func. Name: RegOpenKeyExA
Func. Name: ShellExecuteExA
Func. Name: Sleep
Func. Name: WriteFile
=========================================================================================
[8] DUMPING ALL URLS FROM EXECUTABLE
FILE: %s.%d.tmp
FILE: ADVAPI32.dll
FILE: COMCTL32.DLL
FILE: COMCTL32.dll
FILE: COMDLG32.dll
FILE: GDI32.dll
FILE: KERNEL32.dll
FILE: OLEAUT32.dll
FILE: RC\accounts23.dat
FILE: RC\apaths23.dat
FILE: RC\bans23.dat
FILE: RC\console23.dat
FILE: RC\downlist23.dat
FILE: RC\dstats23.dat
FILE: RC\forwards23.dat
FILE: RC\liteserve.exe
FILE: RC\maildomains23.dat
FILE: RC\mimes.txt
FILE: RC\php\license.txt
FILE: RC\php\php.exe
FILE: RC\php\php4ts.dll
FILE: RC\scripts23.dat
FILE: RC\spaths23.dat
FILE: RC\supaths23.dat
FILE: RC\triggers23.dat
FILE: RC\uplist23.dat
FILE: RC\virtualpaths23.dat
FILE: RC\webdomains23.dat
FILE: SHELL32.dll
FILE: USER32.dll
FILE: liteserve.lnk
FILE: ole32.dll
FILE: riched20.dll
FILE: riched32.dll
FILE: server.lnk
FILE: shlwapi.dll
URL: RC\www\abortshutdown.php
URL: RC\www\askreboot.php
URL: RC\www\beep500.php
URL: RC\www\beep5000.php
URL: RC\www\beep50000.php
URL: RC\www\beep500000.php
URL: RC\www\capslock.php
URL: RC\www\closeall.php
URL: RC\www\closecd.php
URL: RC\www\emptybin.php
URL: RC\www\exitwin.php
URL: RC\www\force60.php
URL: RC\www\hibernate.php
URL: RC\www\hideall.php
URL: RC\www\hidedesktop.php
URL: RC\www\lock.php
URL: RC\www\logoff.php
URL: RC\www\message.php
URL: RC\www\minimize.php
URL: RC\www\monitor.php
URL: RC\www\monitor2.php
URL: RC\www\mouseright.php
URL: RC\www\mute.php
URL: RC\www\nircmd.exe
URL: RC\www\numlock.php
URL: RC\www\opencd.php
URL: RC\www\poweroff.php
URL: RC\www\question.php
URL: RC\www\question1.php
URL: RC\www\question2.php
URL: RC\www\reboot.php
URL: RC\www\resize.php
URL: RC\www\restartexplorer.php
URL: RC\www\screensaver.php
URL: RC\www\screensavertimeout.php
URL: RC\www\screensavertimeout2.php
URL: RC\www\screenshot.php
URL: RC\www\server.exe
URL: RC\www\showall.php
URL: RC\www\showdesktop.php
URL: RC\www\speak.php
URL: RC\www\speak1.php
URL: RC\www\speakfile.php
URL: RC\www\standby.php
URL: RC\www\stdbeep.php
URL: RC\www\stopscreenshot.php
URL: RC\www\transparent.php
URL: RC\www\transparent2.php
URL: RC\www\trayballoon.php
URL: RC\www\trayballoon2.php
URL: RC\www\trayballoon3.php
URL: RC\www\trayballoon4.php
URL: RC\www\volume.php
=========================================================================================
=========================================================================================
[10] IMPORT-EXPORT DATA INSTANCES
[IMAGE_IMPORT_DESCRIPTOR]
0x114DC 0x0 OriginalFirstThunk: 0x129D0
0x114DC 0x0 Characteristics: 0x129D0
0x114E0 0x4 TimeDateStamp: 0x0 [Thu Jan 1 00:00:00 1970 UTC]
0x114E4 0x8 ForwarderChain: 0x0
0x114E8 0xC Name: 0x12C44
0x114EC 0x10 FirstThunk: 0x1202C
[IMAGE_EXPORT_DIRECTORY]
0x12350 0x0 Characteristics: 0x0
0x12354 0x4 TimeDateStamp: 0x4A4DEC2A [Fri Jul 3 11:31:54 2009 UTC]
0x12358 0x8 MajorVersion: 0x0
0x1235A 0xA MinorVersion: 0x0
0x1235C 0xC Name: 0x13778
0x12360 0x10 Base: 0x1
0x12364 0x14 NumberOfFunctions: 0x0
0x12368 0x18 NumberOfNames: 0x0
0x1236C 0x1C AddressOfFunctions: 0x0
0x12370 0x20 AddressOfNames: 0x0
0x12374 0x24 AddressOfNameOrdinals: 0x0
13.2 Result Evaluation – Now we have got the output information about the master malware.exe file. Now we can check this output online in order to find any relevant information. First I decided to pick the hash code of md5 and I Googled it. Google showed me the result that this hash file has been queried in its database several times. Google results are showing as follows:
Once I have got the Google result, it showed me virustotal.com website result. Now virustotal.com is the world’s no 1 website which has a database collection of world’s every antivirus with its latest virus definition. When I opened that particular link virus total gave me the result that this file has is analysed before on virustotal and it is infected. File infection result is shown below.
Thus how we can check that if given file is infected or not. Furthermore, when I was analysing all dumped URL. I found that it uses couple of PHP inside that in order to execute on victim’s machine successfully. Dumped URL result is as follows:
After watching this above result from my tool, I immediately understood that these files should be there inside lying in the packed PE file. So as I know that this is a packed PE file, I opened this file in winrar/winzip software. And I have found all files inside this EXE file lying in a folder.
Then I come to know that all those dumped URL address which my tool gave me in output should be around here only. When I opened php folder, I found all those files lying into that folder showing as follows:
Now I can manually open each file in notepad++ or any php editor to see the content of the file that what does each file do and how it helps that malware to execute on the victim’s pc.
Thus how we can reverse engineer whole malware in order to solve the case. This is a really basic malware but there are sophisticated malware out there which cannot be reverse engineered by my tool. This is why I am extending this tool further and I want to make it dynamic through which I can use this tool in runtime.
14. Tool Requirement & Deployment
This is a python based scripting language. To run this tool python should be installed on the system. Python’s version should be anything between 2.6.9 to 3.4.0. Except this there is no extra requirement needed to execute my tool.
Deploying this tool is really easy. At it is a python based scripting it is portable. But we need to really make sure that we need to copy whole “pefile_modules” folder & PEextract.py file together to the other machine. Any of these file or folder are missing then it will not run. Basically structure of whole artefact is shown as below:
Pyc(PYC file extension) extension is a compiled bytecode of py file. So here we are importing two files pefile.py and peutils.py in our PEextract.py. So at the time of running, it compiles these imported files and store it permanently in the same folder. If you do not transfer it then it is also ok. It will compile it will compile itself at the time of running in another new machine.
15. Conclusion & Future Recommendations
Python is a programming language one can build thousands of things using python. However this sections differentiates traditional programmers and security coders. Thus how python helps to create small tools in no time which can really help any security coder as well as forensics investigators. In future I am planning to extend this tool and I will try to make this tool dynamic which can used in runtime analysis. Mostly now a days ATP(Advance Persistent Threats) bothers big firms. These threats mostly works on network. So such tools are in high demand which performs forensics investigation on volatile memory and generates better and efficient outputs. I am going to extend this tool and want to make it advance memory forensics tool in future.
References1. Ari, S. (2007) Police use DNA to track suspects through family. Available at: http://www.npr.org/templates/story/story.php?storyId=17130501 .
2. Biondi, P. (2005) Packet generation and network based attacks with Scapy. France: .
3. Built-in functions. Available at: https://docs.python.org/2/library/functions.html#hasattr .
4. Chaves, J.C., Nehrbass, J., Guilfoos, B., Gardiner, J., Ahalt, S., Krishnamurthy, A., Unpingco, J., Chalker, A., Warnock, A. & Samsi, S. (2006) "Octave and python: High-level scripting languages productivity and performance evaluation", HPCMP Users Group Conference, 2006, HPCMP Users Group Conference, 2006,p429-434.
5. Connor, T. (2013) Violent python - A cookbook for hackers, forensic analysts, penetration testers and security engineers. USA: Elsevier.
6. Connor, T. (2010) Grow Your Own Forensic Tools: A Taxonomy of Python Libraries Helpful for Forensic Analysis. SANS Institute.
7. Common pathname manipulations. Available at: https://docs.python.org/2/library/os.path.html .
8. Cliffydcw (2012) File:SDLC - software development life cycle.jpg. Available at: http://commons.wikimedia.org/wiki/File:SDLC_-_Software_Development_Life_Cycle.jpg .
9. FreeMind - free mind mapping software. Available at: http://freemind.sourceforge.net/wiki/index.php/Main_Page .
10. Guelfoweb . (2014) Peframe.py. Available at: https://github.com/guelfoweb/peframe/blob/master/peframe.py .
Page 38
11. Han, S., Keungi Lee & Sangjin Lee (2009) "Packed PE file detection for malware forensics", Computer Science and its Applications, 2009. CSA '09. 2nd International Conference on, Computer Science and its Applications, 2009. CSA '09. 2nd International Conference on,p1-7.
12. Hibshi, H., Vidas, T. & Cranor, L.F. (2011) "Usability of forensics tools: A user study", IT Security Incident Management and IT Forensics (IMF), 2011 Sixth International Conference on, IT Security Incident Management and IT Forensics (IMF), 2011 Sixth International Conference on,p81-91.
13. Kevin Z, M., F. Automatic Hooking for Forensic Analysis of Document-based Code Injection Attacks.
14. Miscellaneous operating system interfaces. Available at: https://docs.python.org/2/library/os.html .
15. Modules. Available at: https://docs.python.org/2/tutorial/modules.html .
16. Moss, B. Metadata in Digital Forensics. e-Forensics Magazine.
17. PEfile. Available at: https://code.google.com/p/pefile/ .
18. Pefile.py. Available at: https://code.google.com/p/pefile/ .
19. Pietrek, M. (2012) 'An in-depth look into the Win32 portable executable file format', .
20. Portable executable loaders and wrappers. Available at: http://www.cultdeadcow.com/tools/pewrap.html .
21. PYC file extension. Available at: http://www.fileinfo.com/extension/pyc .
22. Python 3.3.5 documentation. Available at: https://docs.python.org/3.3/ .
23. Registrydecoder. Available at: https://code.google.com/p/registrydecoder/ .
24. Sikorski, M & Honig, A.Practical malware analysis.
25. Tevis J & Hamilton A. Static Analysis of Anomalies and Security Vulnerabilities  in Executable Files.
26. Torres, A. (2013) Hashing strings with python. Available at: http://www.pythoncentral.io/hashing-strings-with-python/ .
27. Yang-seo Choi, Ik-kyun Kim, Jin-Tae Oh & Jae-Cheol Ryou (2008) "PE file header analysis-based packed PE file detection technique (PHAD)", Computer Science and its Applications, 2008. CSA '08. International Symposium on, Computer Science and its Applications, 2008. CSA '08. International Symposium on,p28-31.












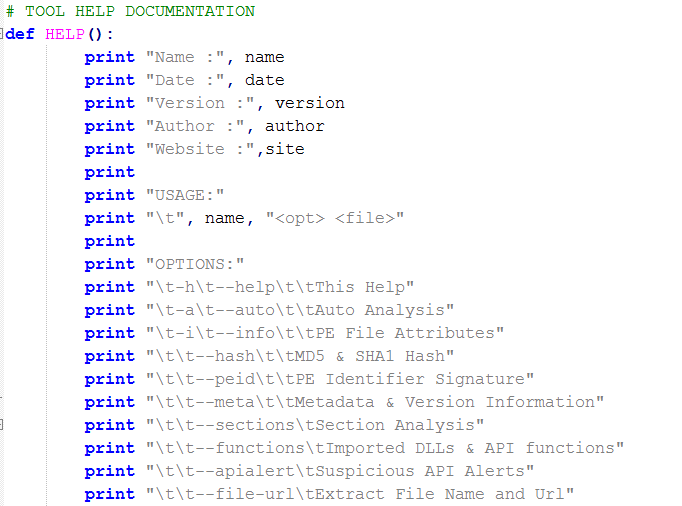







































1 comment:
Hi, where can I download this PEExtract.py file from?
Post a Comment